Only your team gets in. Nobody else.
We built the very first security system for AI-generated apps that authenticates requests before they ever reach the codebase.
A user is not guessing anymore and there’s no blind trust in AI. With us they have a security layer companies can actually depend on.
A user is not guessing anymore and there’s no blind trust in AI. With us they have a security layer companies can actually depend on.
CREATED WITH PYTHAGORA
Control every access point.
Unlike typical no-code or AI builders, Pythagora doesn’t stop at pretty frontends. We’re built for teams who need real software secure, scalable, and tailored to your workflows.
From your first prompt to production, everything stays in your control.
We’ll work with your team to map out your needs, customize the platform, and make sure everything stays in your control.
We’ll work with your team to map out your needs, customize the platform, and make sure everything stays in your control.
Getting started with Pythagora.ai
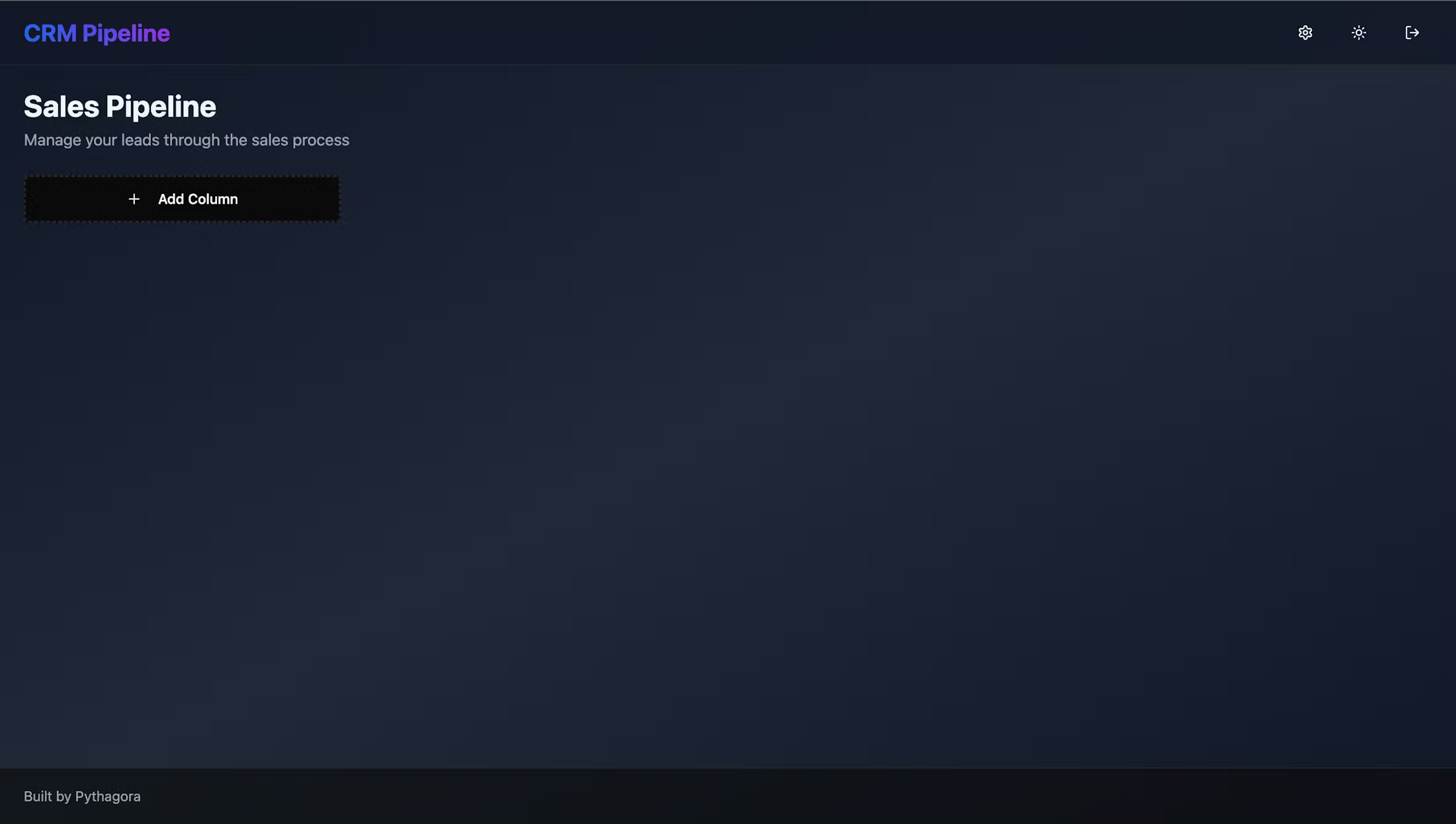
Securely Build and Manage Your Apps
Manager
You register on Pythagora.ai
Manager
Set up the authentication provider
Manager
Add your team
Developer
Start building your apps
Developer
Upon deployment select who has access to the app apps
END USER
Only users you give access to will be able to access those apps






Getting started with Pythagora.ai
Securely Build and Manage Your Apps






Manager
You register on Pythagora.ai
Manager
Set up the authentication provider
Manager
Add your team
Developer
Start building your apps
Developer
Upon deployment select who has access to the app apps
END USER
Only users you give access to will be able to access those apps
PRIVATE SHARING
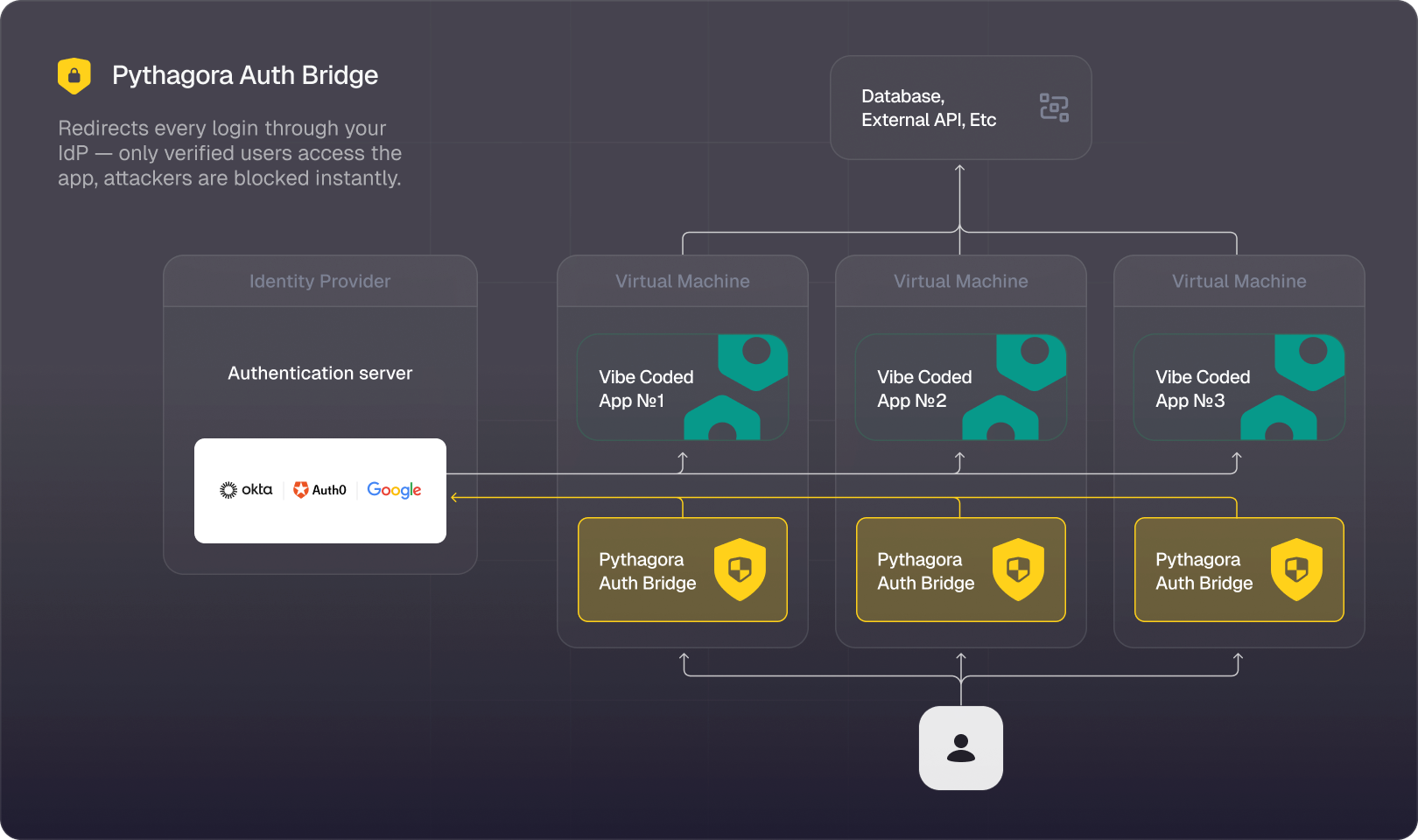
If you don’t approve it, it doesn’t get in.
Access to the apps you've built is enforced at the infrastructure level. Pythagora manages your security, so you don’t have to worry about vulnerabilities or data breaches.
Other AI App Builders
Simple login leaves apps exposed — both users and attackers can get in, putting your system at risk.
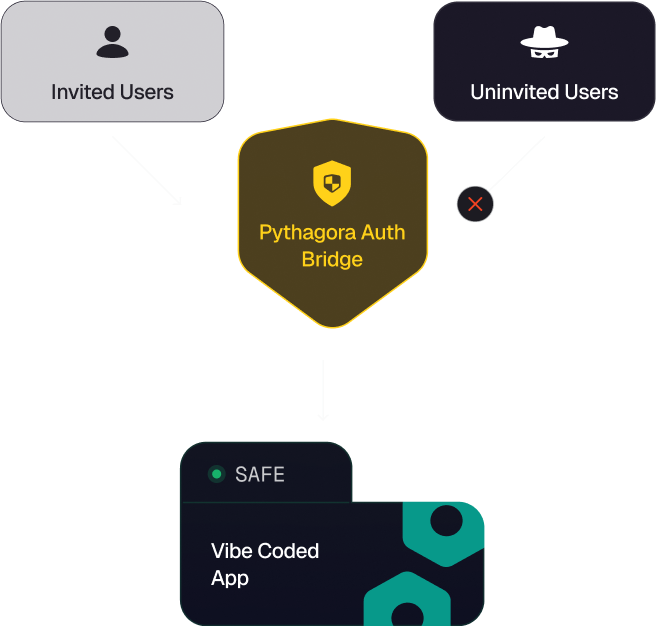
Pythagora Auth Bridge
Verification happens at the gate: invited users are approved via Auth Bridge or SSO, while attackers are stopped instantly.
FEATURE COMPARISON
How we stand out
Feature
Requirements-first development
Complete app architecture
Production-ready AWS infrastructure
Professional debugging tools
Full code ownership & privacy
Enterprise-grade internal tools
Requirements-first development
Other AI App Builders
FEATURE COMPARISON
How we stand out
Feature
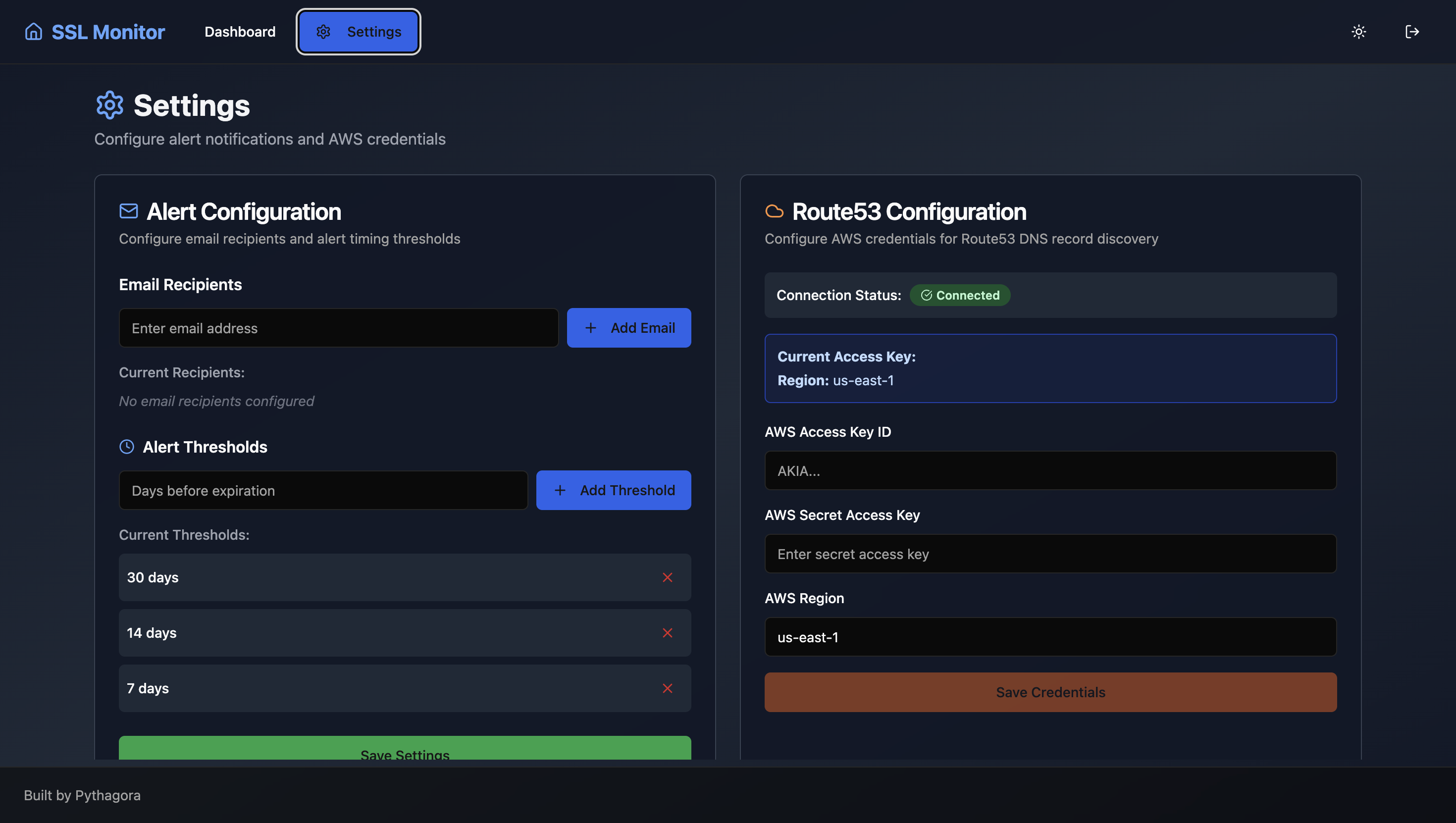
Enterprise-Grade Authentication
Reverse Proxy Protection
Internal Deployments
Internal Tool Focus
Transparent Control
Other AI App Builders
Integrates with Google or internal DBs
Requests blocked before reaching backend if not authenticated
Email-based user invites; full access control per tool
Secure dashboards, workflows, and sensitive operations
No black-box Al. Full visibility over security & access. Audit control (who access which tools when)

Authentication buried in Al-generated code; hard to audit
Requests often reach backend directly; risk of exposed endpoints
Limited or no control over who can access deployed apps
Designed for demos or prototypes, not production workflows
Security handled inside Al codebase; unclear what's protected
EXAMPLES